
Contents:
- What is Let’s Encrypt?
- Why use Let’s Encrypt?
- Why shouldn’t you use Let’s Encrypt?
- In conclusion… DV vs OV vs EV: What’s really the difference?
No doubt you’ve heard of Google’s recent update regarding HTTPS, and their ongoing quest to create a more secure internet for us to inhabit.
As of October 2017 (Chrome 62), Google Chrome will be displaying the “Not secure”warning to users entering data on a HTTP page, as well as all HTTP pages in Incognito.
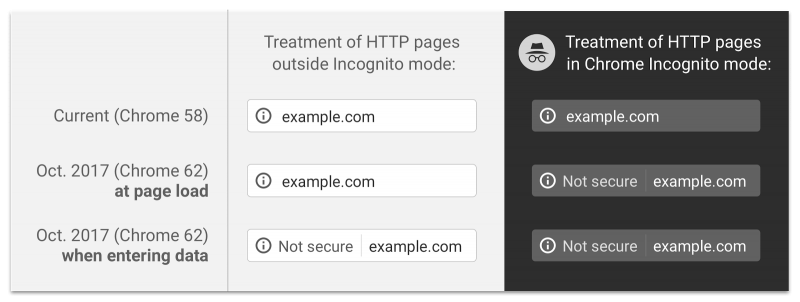
Their latest effort to encourage website owners still using HTTP to get it together, and get on HTTPS! (As if user security and SEO benefits wasn’t enough…)
But simply installing an SSL certificate is no walk in the park…

What is Let’s Encrypt?
Launched in 2016, Let’s Encrypt is a certificate authority offering a free solution to TLS (Transport Layer Security) encryption for website owners. The Let’s Encrypt initiative was founded on the objective to provide all website owners with SSL certificates that are not only free, but both easy to install and easy to update too.
Encrypting the traffic to your website used to be a fairly expensive ordeal. Particularly for small business owners who want to do right by their website visitors, but don’t have a great deal of money to invest in HTTPS. Let’s Encrypt tackles this head-on, additionally eliminating the complexity of installing and maintaining the security certificates with automated processes.
Why use Let’s Encrypt?
The biggest selling point of Let’s Encrypt is obvious… It’s FREE!
It’s a fairly simple installation process, far simpler than traditional SSL certificates, designed to make HTTPS encryption accessible to any website owner. For Linux web servers where you have shell access, there are only two commands to be executed in order to acquire and install the Let’s Encrypt certificate. Many popular hosting companies, however, do not allow their customers root access but customers instead manage their website through a control panel with a graphic user interface, such as cPanel or Plesk. In this case, you may find that your hosting provider has already included built-in support for the obtainment and configuration of the free SSL certificate, as well as automating renewals, via a plugin in the control panel. They basically request the free certificate on your behalf, then automatically handle the maintenance themselves. Some web hosting companies now even automatically install the certificate on behalf of all their customers by default.
Certbot automatically fetches and deploys your Let’s Encrypt certificate, to immediately start serving over HTTPS. You can even enable features such as automatic HTTP to HTTPS redirects on Apache. As an initiative from EFF (Electronic Frontier Foundation), Certbot is part of a web-wide effort to encrypt the entire internet for the safety and security of its users.
It does what it says on the tin: it provides a secure connection between your site visitors and your site server.
Furthermore, they have respectable documentation available for those who need it, and a vast amount of community support when you need more specific information and advice.
Google Chrome are “platinum sponsors” of Let’s Encrypt, so there’s little chance that Chrome will distrust it anytime soon. Unlike Symantec certificates (operating under brand names: VeriSign, Equifax, GeoTrust, RapidSSL, and Thawte), which did not comply with CA/Browser Forum Baseline Requirements and are therefore being distrusted by Google in future Chrome updates.
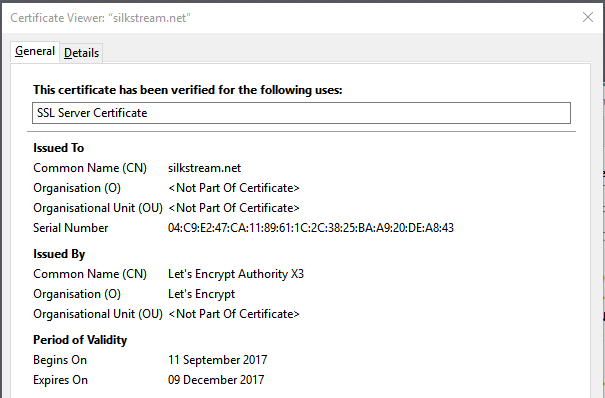
If you look at our Let’s Encrypt SSL certificate, you may notice the Period of Validity seems extremely short. It’s definitely on the shorter side when compared to other popular SSL certificates. The 90 day lifetime can be seen as a disadvantage as for some it’s an inconvenience, but it’s definitely pro-security as it requires a key change every three months.
Let’s Encrypt’s SAN certificates (Subject Alternative Name) allows for multiple domain names to be protected with a single certificate. The ability to add multiple SAN values to a single Let’s Encrypt certificate can be a time-saver for organisations with multiple websites or microsites. This is different from wildcard certificates that apply to multiple subdomains, but not entirely different domains. (More on wildcards later…)
There is also no downtime when issuing the certificate, due to the ACME protocol which performs the server validation.
Why shouldn’t you use Let’s Encrypt?
The biggest issue is that, although Let’s Encrypt provides the modern standard of website encryption, it doesn’t offer Extended Domain Validation (the green bar beside the URL, displaying the company name next to the padlock). There’s a difference. Not only does this mean that the identity of the website is not verified to the same extent as a website with Extended Domain Validation but, to the user (no matter how clueless), they may place less trust in websites that do not have the full “green bar” displaying the company name. As it is just domain validation, there are no additional checks on the owner of the domain or website.
What’s more, if Extended Domain Validation SSL certificates (EVs) or Organisation Validation SSL certificates (OVs) are important to you, you should be aware that Let’s Encrypt have no plans on making OVs and EVs available.
How EV certificates display in various browsers
Chrome:![]()
Edge:
![]()
Firefox:
![]()
Internet Explorer:
![]()
Let’s Encrypt also do not currently supply Wildcard SSL certificates (as of November 2017). This, however, will be available from January 2018. So don’t let that put you off completely, if this is the reason you’re on the fence. For now though, the disadvantage to not having wildcard SSL is that you will need separate SSL certificates for multiple subdomains. If it’s not quite January 2018 when you’re reading this and you urgently need HTTPS across all your subdomains—such as blog.website.com, www.website.com, payment.website.com, etc—then too bad.
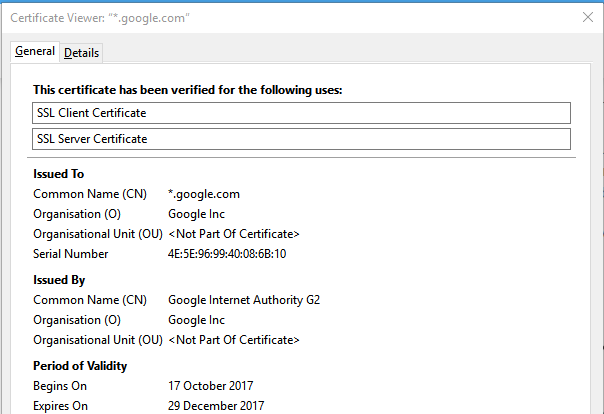
Notice the *.google.com
As mentioned before, the 90 day lifetime (though good for security) can be a real disadvantage if your web server doesn’t automate issuance. Commercial SSL certificates tend to have a longer lifetime. This isn’t really a big deal at all if the process is automated but, if you have to remember to do so manually every 90 days, let’s be honest… It’s a real chore, and you’ll be tempted to just let it expire.
Though some hosting companies provide off-the-shelf Let’s Encrypt setup, many more (such as Namecheap and Hostgator) do not. Why would they when they sell SSL certificates as a service? So if you’re a newbie with all this, the DIY workaround may prove a little challenging.
There are also compatibility issues with some platforms such as older versions of Blackberry, Windows XP, Nintendo 3DS, PS3, and so on… For the majority of website owners, this is a non-issue. You might even let slip a giggle at the thought. But it’s still worth a mention, because you never know.
If you’re a large website, you may also need to rely upon frequent customer support… As you can expect from a non-profit, they do lack strong customer support. Commercial providers, on the other hand, have the resources to dedicate more time to their paying customers. If you don’t have a tonne of experience with SSL certificates, the customer support alone could be well worth the higher price.
For developers managing multiple client websites, the rate limit can also be an inconvenience. There is, however, a Renewal Exemption to ensure that users are always able to renew a certificate without it counting toward the weekly rate limit. Renewals are defined as containing “the exact same set of hostnames as a previously issued certificate”.
According to Let’s Encrypt, the rate limits are as following:
- 20 certificates per registered domain per week
- 100 names per certificate
- 5 duplicate certificates per week
- 10 accounts per IP address per 3 hours
- 500 accounts per IP range within an IPv6 /48 per 3 hours
- 300 pending authorisations on your account
There is no way to temporarily reset the rate limit if you’ve hit it. (Revoking certificates will not reset your rate limits either, if you’re thinking of getting cheeky.) Though you can request a higher rate limit in advance if you are a large organisation or hosting provider, but requests can take weeks to process.
Though this doesn’t directly affect how Let’s Encrypt SSL certificates work on your websites, some website owners are against the use of Let’s Encrypt based on the principle. Why, you ask? Let’s Encrypt came under fire in 2016 for making HTTPS too easy, thereby providing a false sense of security to users. In other words, any malicious website can install the free SSL certificate without much scrutiny or financial investment, and exploit the appearance of “looking more trustworthy” to push malware to unsuspecting visitors. This isn’t really a fault of Let’s Encrypt, but rather the fault of a lack of general education regarding internet safety. Just because a website says it’s “secure” doesn’t mean that the website is well-intentioned, and some cybercriminal opportunists are abusing this common misconception to trick those less web-savvy into giving away sensitive information and downloading gosh-knows-what. It’s all very well that big companies like Google are pushing for secure connections online, but there does need to be more effort made in informing casual users exactly what this means.
In response to this criticism, in 2015 Let’s Encrypt commented:
“Since we announced Let’s Encrypt we’ve often been asked how we’ll ensure that we don’t issue certificates for phishing and malware sites. The concern most commonly expressed is that having valid HTTPS certificates helps these sites look more legitimate, making people more likely to trust them.
Deciding what to do here has been tough. On the one hand, we don’t like these sites any more than anyone else does, and our mission is to help build a safer and more secure Web. On the other hand, we’re not sure that certificate issuance (at least for Domain Validation) is the right level on which to be policing phishing and malware sites in 2015.”
But is it really the responsibility of certificate providers to educate the users, or does this obligation lie with the web browsers?
In conclusion…
When Let’s Encrypt is installed correctly, it’s certainly better than nothing.
Do you get what you pay for? Sure! But the value is subjective. Large e-commerce sites or sites handling sensitive data should absolutely be considering paid SSL certificates. For small business websites or Average Joe Blogger, Let’s Encrypt provides a great, free alternative that you might as well take advantage of and, at the very least, benefit from the added SEO value.
The biggest question really is: what are your requirements from an SSL certificate?
DV vs OV vs EV: What’s really the difference?
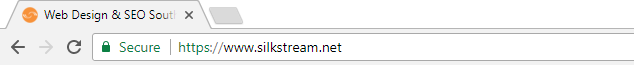 Silkstream uses Let’s Encrypt (DV certificate)
Silkstream uses Let’s Encrypt (DV certificate)
Domain Validation (DV Certificates) is the quickest and cheapest option, but has the lowest level of authentication. Company information isn’t checked or displayed on the SSL certificate but, for small business and personal websites that don’t require extensive credibility, the basic encryption and HTTPS is all you will ever really need.
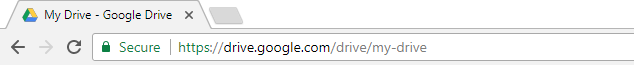
Google’s wildcard SSL displays organisation info, but no green bar
Organisation Validation (OV Certificates) aren’t issued as liberally as DV ones as the Certificate Authority checks the credibility of the organisation or individual applying for the certificate, and the company information will be displayed to the website visitors on the certificate. This gives the website visitor more visible trust in the organisation – if they know what they are looking for. Otherwise, there is no real visual differentiation between DV and OV at a glance.
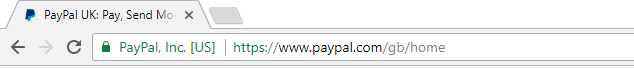
PayPal uses a Symantec Class 3 EV SSL certificate
Extended Validation (EV Certificates) are the ultimate SSL certificates when it comes to security, as they require the Certificate Authority to check the organisation or individually much more thoroughly prior to issuance. This is the SSL certificate that gives the website the “green bar” next to the address bar, displaying the company name. Large e-commerce sites that handle sensitive data, such as credit card information, should definitely be investing in this type of certificate. Especially as a well-known public-facing organisation, your commitment to web security shows your users and customers that you care about the privacy of their information, boosting your credibility. This in turn can result in a lower cart abandonment rate and a higher sense of user trust placed in your company.

